NYU researchers developed an AI that can imitate fingerprints to bypass biometric readers
It seems that every smartphone has a fingerprint reader, and with good reason. Biometrics are more difficult to crack than traditional passwords, making fingerprint readers difficult systems to crack. After all, there are so many factors in a fingerprint that correctly recreating it at random would be nearly impossible. Well, unless you use the AI software developed by a research team at NYU.
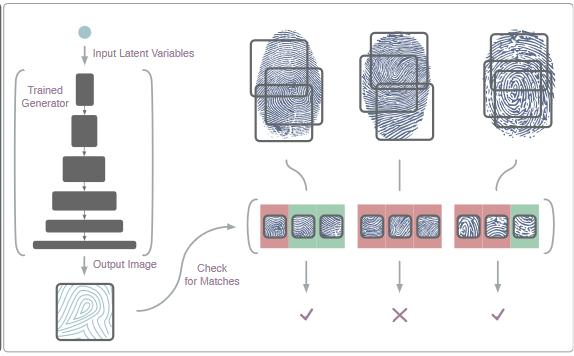
In a paper presented at the recent BTAS 2018 security conference in LA, a research team from New York University showed off an AI program that could recreate fingerprints used in a biometric security system with a 20% success rate. The AI, dubbed “DeepMasterPrints,” uses a library of partial fingerprint images to reconstruct and test imitated fingerprints for a particular biometric system. DeepMasterPrints uses a method similar to a “dictionary attack,” a form of password cracking.
In a dictionary attack, an algorithm takes hashed passwords and tries them against a massive library of known passwords with slight variations until it finds an iteration that passes the hash. In other words, the computer runs a list of known passwords and tries them against the password hash. If the trial fails, then the system will alter the password slightly (such as capitalizing a letter or using a different number) and try it again. This process repeats until the program finds a password that passes the hash correctly.
DeepMasterPrints works in similar fashion. However, instead of permuting strings of text, DeepMasterPrints takes a large library of fingerprints and slightly alters different factors until it finds a match.
To do this, DeepMasterPrints takes advantage of flaws inherent to most fingerprint readers. Modern readers only scan a portion of a user’s fingerprint, limiting the number of possibilities and reducing the workload for a system like DeepMasterPrints. These partial scans typically capture similar regions of a fingerprint between users, and these smaller regions usually have a number of similarities between them.
This is a rough summary of how the system works. For full details, you can read the full research paper here. The key takeaway is that DeepMasterPrints was able to guess fingerprints about 20% of the time, far beyond most fingerprint scanners' rating of a 0.1% error rate.
So does DeepMasterPrints invalidate fingerprint scanners as a security measure? Not really. The researchers freely admit that while someone could eventually use something like DeepMasterPrints to hack into something like a smartphone or computer, they would need to do a lot of work to optimize the AI for a specific system. While the flaws used by DeepMasterPrints are typical for fingerprint readers, each reader is still different. One reader can scan a completely different region than another reader, making optimization a major hurdle to overcome.
Still, considering the lengths some hackers will go to break into a system, fingerprint cracking may not be far off.
}})